Compromise Of System Or Server Integrity Is
Compromise of system or server integrity is. A web server is used to provide a remote root shell for system administration. Server Software Component. SIP is a security technology in macOS that restricts a root user from performing operations that may compromise system integrity.
In a few simple steps you can install the WordPress Security Plugin. On the other hand indicators of attack could simply be system or network evidence that the server is facing an incoming attack such as flood SQL. Use verification of distributed binaries through hash checking or other integrity checking mechanisms.
Enforce complex business rules. The number 65537 is an acceptable compromise between speed and reliability. File system consistency is one of the common ones.
Encrypted client-server communication protection of privacy and integrity with AES and RSA in details. In my opinion the biggest limits on attack surface reduction as a defensive strategy are. Windows Server 2022 Windows Server 2019 Windows Server 2016 Windows Server 2012 R2 Windows Server 2012.
Install the WordPress Security Plugin. Enforce referential integrity across nodes in a distributed database. Maintaining an audit trail of system activity logs can help identify configuration errors troubleshoot service disruptions and analyze compromises that have occurred as well as detect attacks.
We found that the vulnerability lies in how Apple-signed packages with post-install scripts are installed. Multiple ways of delivering exploit code to a browser exist including. If RDP is utilized set RDP connection encryption level to high.
In this article. A phone apps purpose is to make a shell available to the user.
Eternal vigilance is the price of security.
In a few simple steps you can install the WordPress Security Plugin. In this article. Even simple bugs in your code can result in private information being leaked and bad people are out there trying to find ways to steal data. Windows Server 2022 Windows Server 2019 Windows Server 2016 Windows Server 2012 R2 Windows Server 2012. This page allows you to roll virtual dice using true randomness which for many purposes is better than the pseudo-random number algorithms typically used in computer programs. Maintaining an audit trail of system activity logs can help identify configuration errors troubleshoot service disruptions and analyze compromises that have occurred as well as detect attacks. A shell script uses expect to interact with a binary that requires a terminal for inputoutput. Enforce referential integrity across nodes in a distributed database. Where security classified discussions occur entities must undertake.
SQL Server Maintenance plans - Maintenance plans are part of SQL Server out of the box unless youre running Express Edition. Checking at a set point in time with respect to the different types of triggers and guarantees that triggers cannot compromise integrity constraints. There are a number of attack vectors for the operating system of a CA server and the response depends on many factors. Their attributes include the system event the type of schema object and its name. Technical surveillance countermeasures TSCM protect security classified discussions from technical compromise. Use this software to replicate and integrate data from your NonStop database into heterogeneous databases on other server types. A web server is used to provide a remote root shell for system administration.
.jpeg)


.jpeg)












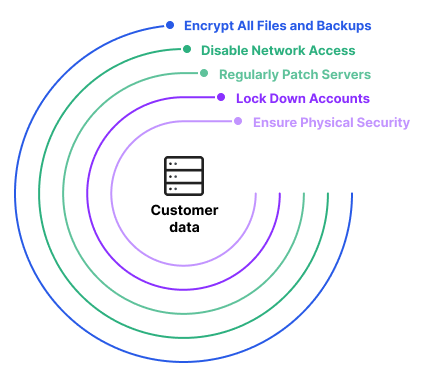









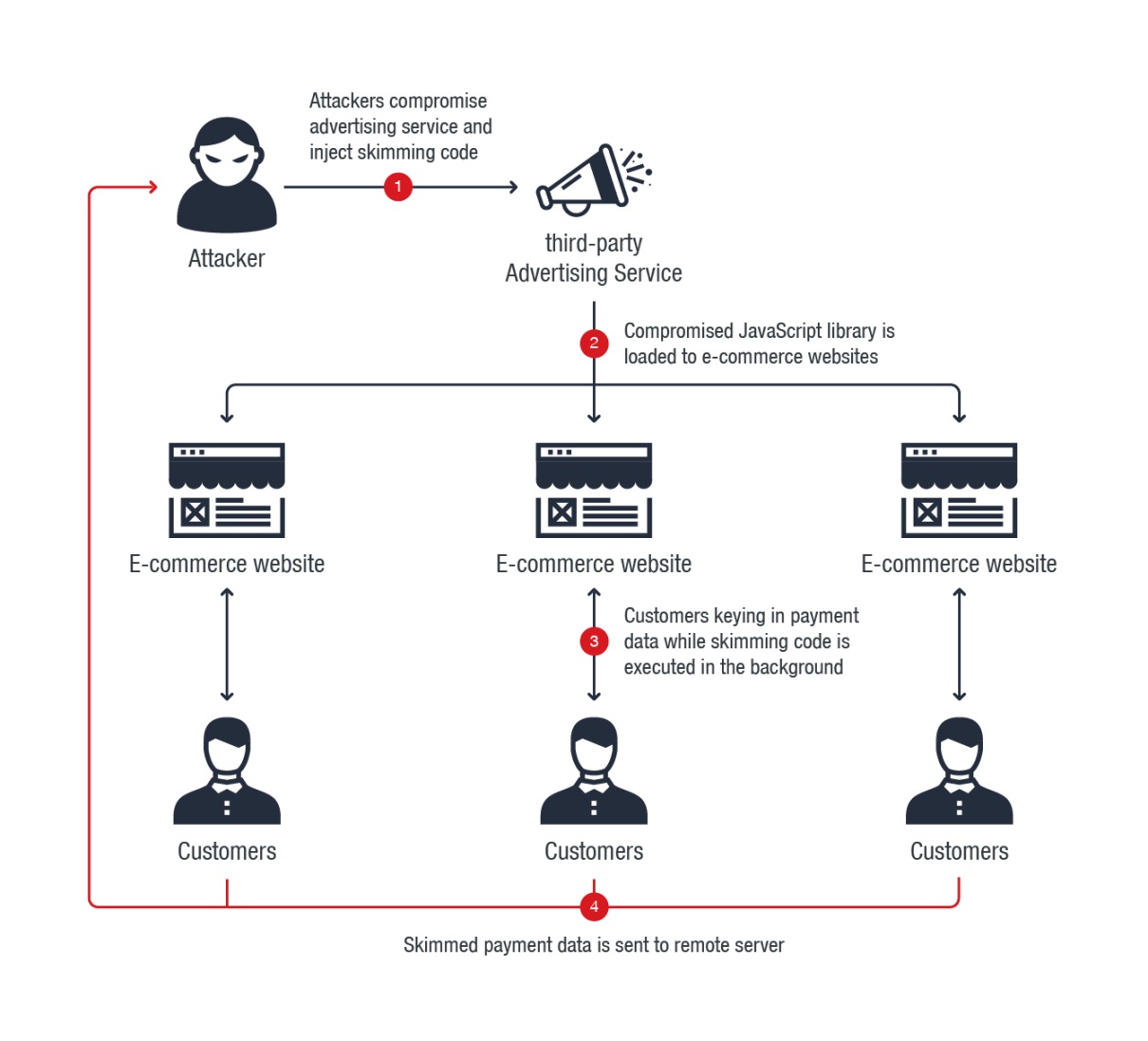










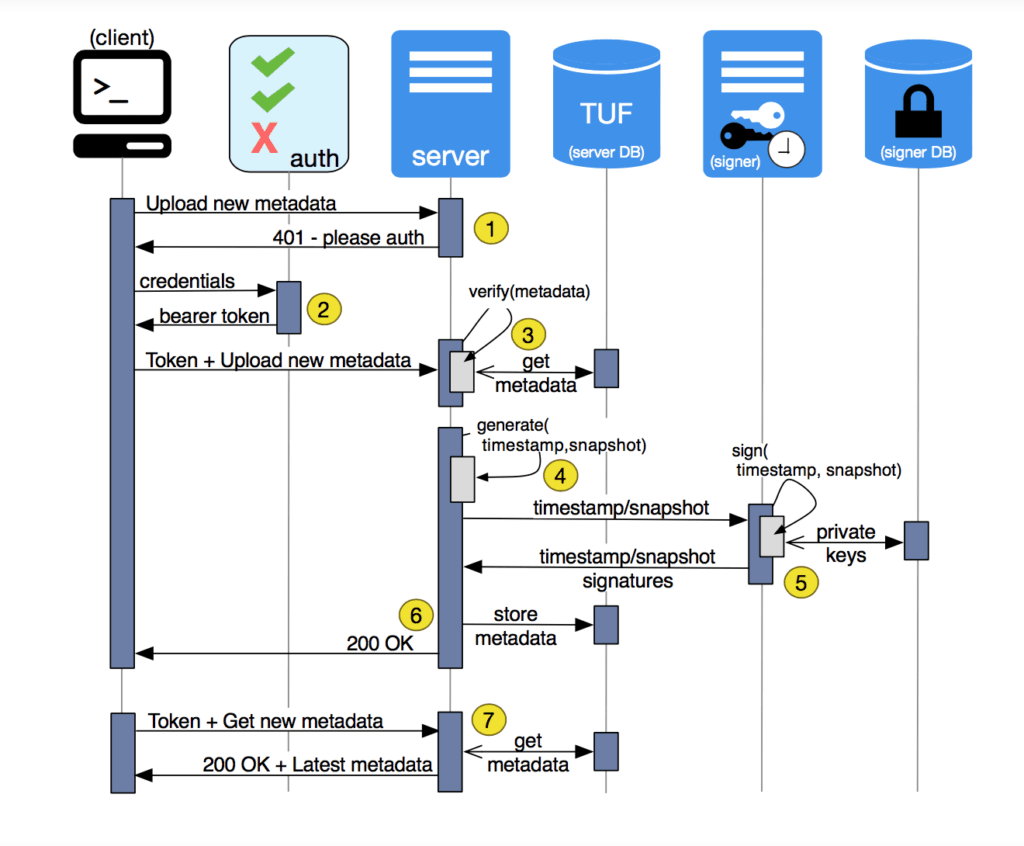

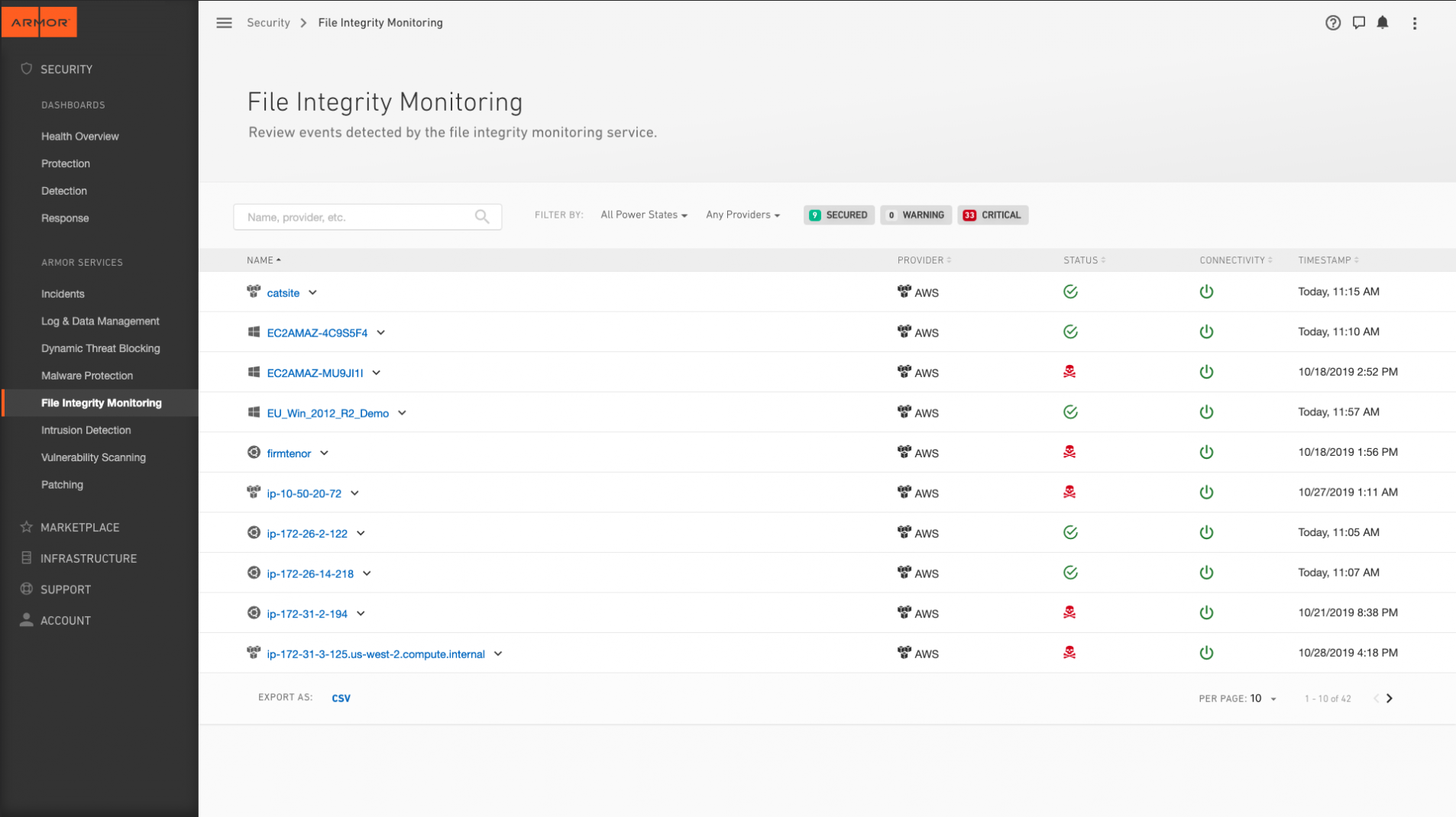


Post a Comment for "Compromise Of System Or Server Integrity Is"